|
Navigation
|
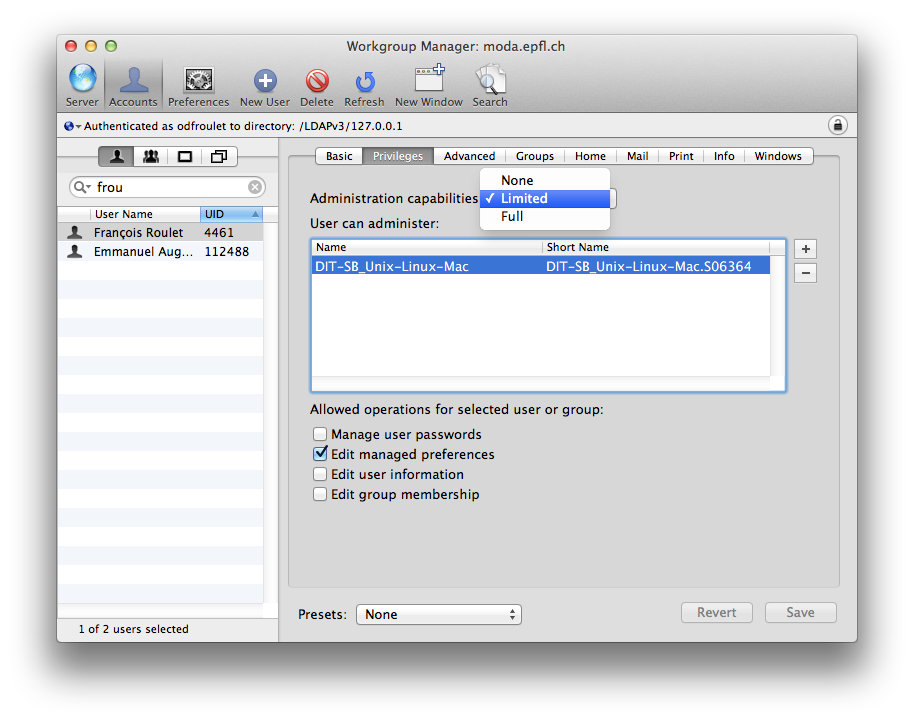
Délégation des droits d'accès. Les administrateurs de Open Directory @EPFL, membres du groupe "OpenDirectory-Admins", sont promus "Administrateurs à droits restreints", ce qui leur confère la possibilité d'atttribuer des MCX des utilisateurs, et à des groupes d'utilisateurs.
Opérations autorisées:
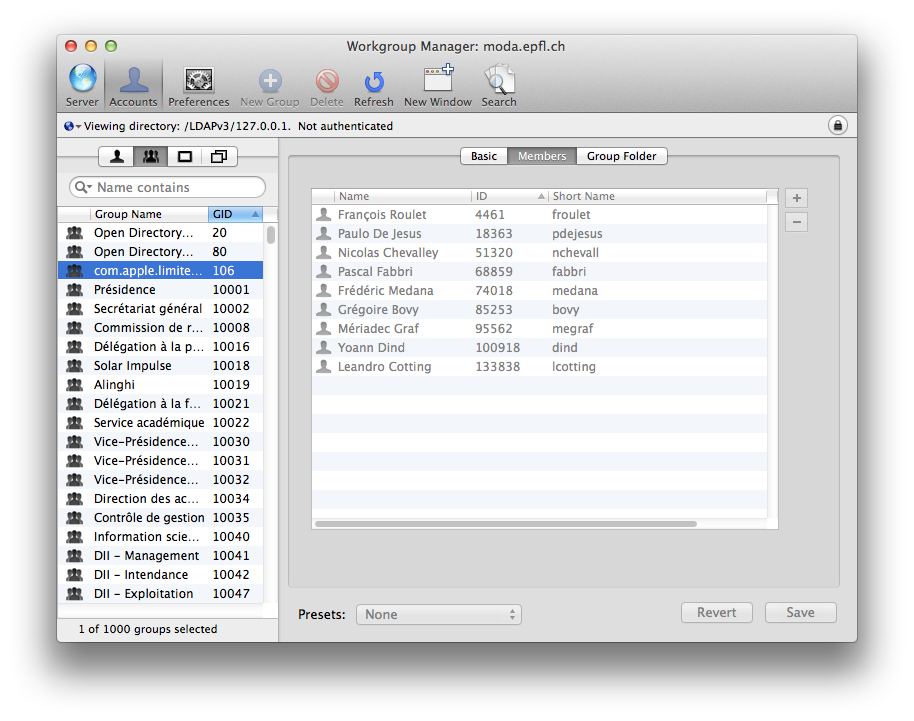
Les utilisateurs qui disposent de droits d'administration limités (limited rights), hérités de la version 10.6, sont automatiquement ajoutés au groupe com.apple.limited_admin . A défaut, depuis la version 10.8, il suffit de les rajouter. Ceci leur confère le droit de se connecter à l'annuaire par WGM.
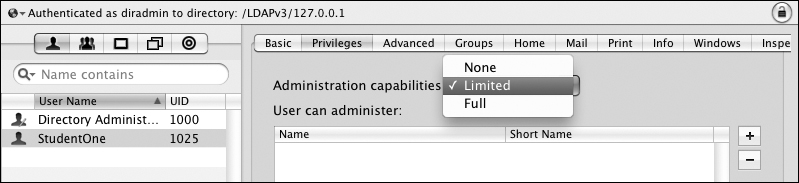
Managing Data Stored in an Open Directory MasterWorkgroup Manager is the main graphical application you use to edit the data stored in the Open Directory master’s directories, but Mac OS X Server also offers a series of command-line utilities to help you import and export data. In this section, you will learn how to use Workgroup Manager to assign limited directory administration privileges to users, as well as explore the DACLs (directory access control lists) that Workgroup Manager creates to enforce these limited administrative privileges. DACLs can also be referred to as directory access controls (DACs) and LDAP access control lists (LDAP ACLs). You will learn how to use ldapadd to add new entries to the LDAP data store, and contrast ldap* tools with such slap* tools as slapadd. To better determine which is best for your situation, you will compare these tools to dsimport (which was introduced in Chapter 1, “Accessing the Local Directory Service”) for adding users to the Open Directory master. Defining Limited AdministratorsOne of the new features of an Open Directory master with Mac OS X Server v10.5, continuing with v10.6, is the ability to give very granular administrative privileges to individual users and groups. When you use Workgroup Manager to set the privileges, Workgroup Manager dynamically edits the DACLs to make the changes effective immediately. The LDAP service evaluates each LDAP request against the DACLs to determine the level of authorization that it should extend to the request. If you use Workgroup Manager or the Directory application as a limited administrator and attempt to modify an attribute you are not authorized to write, you will not be able to complete the modification. It can be very useful to assign a user to have administrative capabilities for a group, to free some of your time for other tasks. Be careful when assigning capabilities; you may not want to enable a limited administrator to change another user’s password or to change their managed preferences. Note that a limited administrator in Mac OS X v10.5 and v10.6 is limited in regards to all methods of LDAP access. Previously, in Mac OS X v10.4 and earlier, a limited administrator was limited only when using Workgroup Manager; the standard LDAP tools would allow that limited administrator full control over the entire LDAP database. To create a limited administrator, do the following:
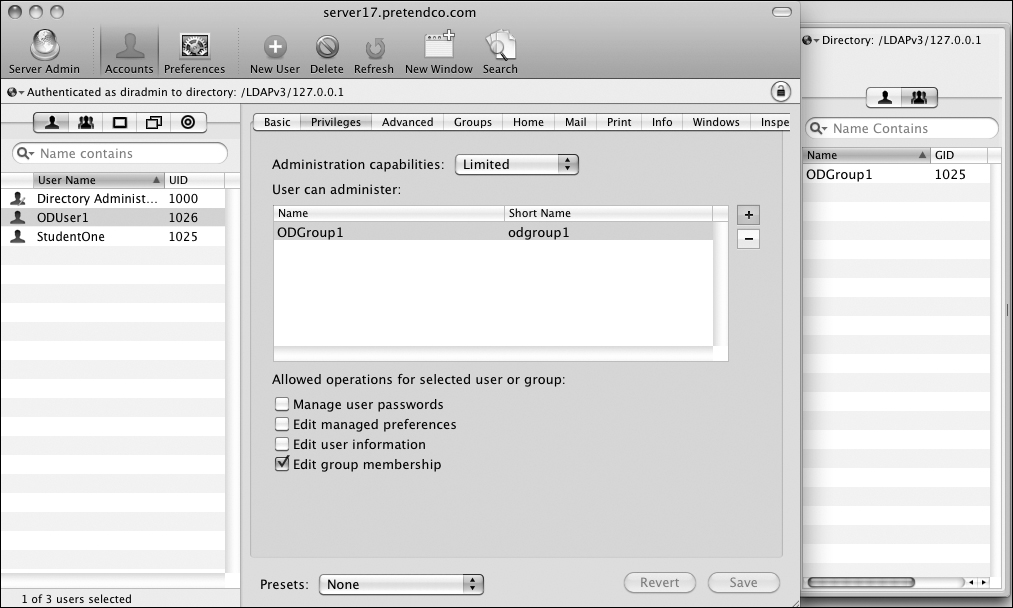
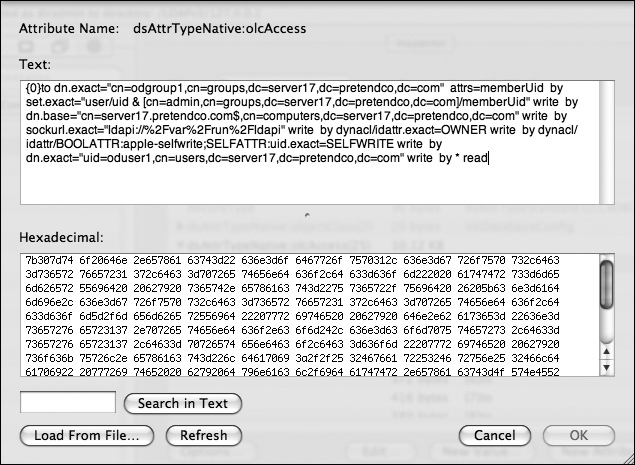
Inspecting the Resulting DACLsA new Open Directory master comes preconfigured with several DAC rules. When you add the ability for one user to edit the group membership for a group, Workgroup Manager creates three new rules granting write access for the user to each of these attributes for the group: memberUID, apple-group-memberguid, and apple-group-nestedgroup. Here is how to use Workgroup Manager to inspect one of the rules:
{0}
to dn.exact="cn=odgroup1,cn=groups,dc=server17,dc=pretendco,dc=com"
attrs=memberUid
by set.exact="user/uid & [cn=admin,cn=groups,dc=server17,dc=pretendco,dc=com]/memberUid" write
by dn.base="cn=server17.pretendco.com$,cn=computers,dc=server17,dc=pretendco,dc=com" write
by sockurl.exact="ldapi://%2Fvar%2Frun%2Fldapi" write
by dynacl/ldattr.exact=OWNER write
by dynacl/idattr/BOOLATTR:apple-selfwrite;SELFATTR:uid.exact=SELFWRITE write
by dn.exact="uid=oduser1,cn=users,dc=server17,dc=pretendco,dc=com" write
by * read
|